Wolfgang Ettlinger & Alexander Hurbean
Skynet wants your Passwords! The Role of AI in Automating Social Engineering
#1about 2 minutes
Understanding the dual role of AI in cybersecurity
Artificial intelligence can be used for both defensive security solutions and for malicious attacks like developing malware.
#2about 3 minutes
The threat of AI-generated deepfakes and voice cloning
Increasingly realistic AI-generated content, such as deepfakes and cloned voices, is being used for CEO fraud and fake kidnapping scams.
#3about 4 minutes
Automating social engineering with autonomous AI agents
Autonomous agents like AutoGPT can be programmed with a single goal to execute complex, multi-step social engineering attacks at scale.
#4about 5 minutes
A framework for automated phishing using LLMs
By jailbreaking models like ChatGPT, attackers can automate the creation of convincing phishing emails by feeding the model target information.
#5about 11 minutes
Building a proof-of-concept AI phishing email generator
A demonstration shows how a tool uses an LLM and service enumeration via DNS records to generate highly targeted phishing emails.
#6about 7 minutes
How to defend against AI-powered attacks
Defenses include user awareness, verification processes like S/MIME and PGP, adopting passkeys, and attempting prompt injection attacks on suspected bots.
Related jobs
Jobs that call for the skills explored in this talk.
Matching moments
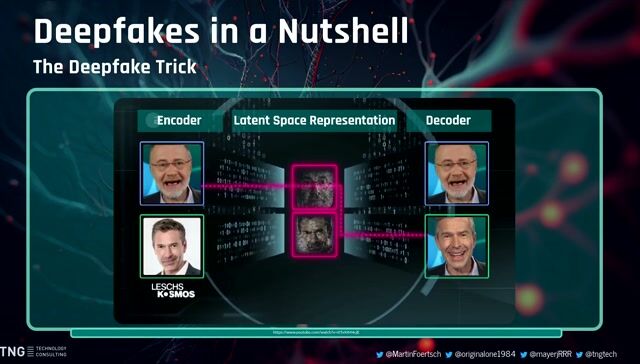
03:11 MIN
Demonstrating deepfake attacks and social engineering
The AI Elections: How Technology Could Shape Public Sentiment
04:07 MIN
How AI accelerates and sophisticates cyber attacks
Tackling the Risks of AI - With AI

03:48 MIN
The perfection of social engineering with generative AI
WWC24 - Chris Wysopal, Helmut Reisinger and Johannes Steger - Fighting Digital Threats in the Age of AI

04:47 MIN
Protecting your online identity from AI-powered scams
WeAreDevelopers LIVE - Accessibility isn't magic, Longevity, Devrel in times of AI and more
04:40 MIN
How attackers use AI to refactor exploits
The AI Security Survival Guide: Practical Advice for Stressed-Out Developers
05:17 MIN
Manipulating AI with prompt injection and hidden commands
WeAreDevelopers LIVE - Is Software Ever Truly Accessible?

02:43 MIN
The evolving cybersecurity landscape with AI
Fireside Chat with Cloudflare's Chief Strategy Officer, Stephanie Cohen (with Mike Butcher MBE)

05:19 MIN
The rise of audio deepfakes in personal and corporate scams
Deep Fakes: The Lies We Can’t See
Featured Partners
Related Videos
 24:49
24:49Deep Fakes: The Lies We Can’t See
George Proorocu
 24:23
24:23A hundred ways to wreck your AI - the (in)security of machine learning systems
Balázs Kiss
 24:14
24:14WWC24 - Chris Wysopal, Helmut Reisinger and Johannes Steger - Fighting Digital Threats in the Age of AI
Chris Wysopal, Helmut Reisinger & Johannes Steger
 30:02
30:02The AI Elections: How Technology Could Shape Public Sentiment
Martin Förtsch & Thomas Endres
 27:02
27:02Hacking AI - how attackers impose their will on AI
Mirko Ross
 30:36
30:36The AI Security Survival Guide: Practical Advice for Stressed-Out Developers
Mackenzie Jackson
 29:28
29:28Tackling the Risks of AI - With AI
Kai Grunwitz, Klaus Bürg & Tomislav Tipurić
 27:10
27:10Manipulating The Machine: Prompt Injections And Counter Measures
Georg Dresler
Related Articles
View all articles



From learning to earning
Jobs that call for the skills explored in this talk.




Commerz Direktservice GmbH
Duisburg, Germany
Intermediate
Senior

Association Bernard Gregory
Canton de Nancy-2, France
Data analysis
Machine Learning

Government of The United Kingdom

webLyzard
Vienna, Austria
DevOps
Docker
PostgreSQL
Kubernetes
Elasticsearch
+2

Crossover
Kiel, Germany
Remote
€100K
Senior
Node.js
